
A core element of blockchain technology is the way transactions are authorised and users are identified. This is different from verifying data or information on the blockchain. This is called 'mining'.
Miners use the hashing puzzle to verify information on the blockchain. Authorisation and identification is the (next) step after the miner has verified the data on the blockchain.
In this article, I will address the question of how transactions are authorised. I will first discuss the concept of 'encryption'. The 'public and private key' is a central element of encryption. In addition, I will discuss the hashing technique in combination with the concept of encryption. This combination is also called the 'digital signature'.
In order to authorise a transaction, the blockchain must know to whom the transaction is addressed. The aim is to uniquely identify owners and properties and ensure that only the rightful owner has access to his or her property. Think of the example of a PO Box: the deliverer of a letter knows the address of the recipient and delivers the letter to the PO Box. If this letter is delivered in the letter box, only the owner of the letter box can access it. The owner of this PO Box has a key to open his PO Box. The same concept also applies to the blockchain. Anyone can send letters to this letterbox (and also visible to everyone). But it is only the owner of this letterbox who can access these letters. The combination of a public letterbox on the one hand and a private key on the other hand is also called 'public-private key encryption' on the blockchain.
The sender who sends a message via the blockchain uses the public key to identify the recipient. This public key is visible to everyone. However, only the recipient who has the corresponding key can see the message. This prevents unauthorised users from gaining access to the message that is not intended for them (such as a safe). The (secure) sending of a message, for example, is called 'encryption' and the opening of this message is called 'decryption'.
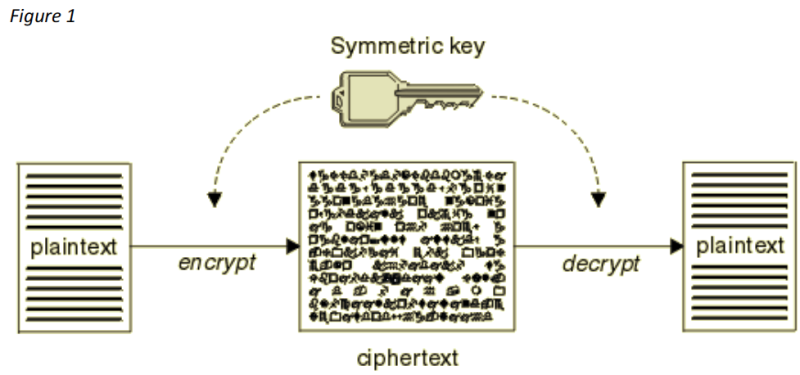
Suppose I send the following message: 'intelligence lockdown'. This message is then 'locked' into a so called cipher text (encrypted text) using a public key of the sender. A cipher text is a message with all kinds of numbers and symbols without any meaning. When this message arrives at the receiver, the receiver has the same (public) key to unlock this cipher text. This is also called symmetric encryption. This was not secure because one key is used to lock and unlock the cipher text. Because of this problem, the asymmetric encryption was born.
Asymmetric encryption always uses two complementary keys. But there is a trick: cipher text created with one of these keys can only be deciphered with the other key and vice versa. By way of illustration:
With asymmetric encryption, the sender and receiver do not have the same key. With asymmetric encryption, the sender and receiver have different keys (public and private key). For example, the sender uses the public key to convert the message into a cipher text. In that case, the receiver does not use the same public key of the sender, but uses the private key to unlock the cipher text. This can also be done the other way round (public to private or private to public). The sender locks the message using his own private key. The receiver then unlocks this cipher text using his own public key. This ensures that you never have to use the same key again to unlock a cipher text that has also been used to lock the message.
If public-private key encryption is combined with the hashing technique, it is called digital signature. This provides an extra layer of security. How does this work?
Suppose A wants to send the message: 'intelligent lockdown' to B. This message will be hashed first. This is the process of converting a certain input (such as this message) into output (a series of numbers and letters). The hash value of intelligent lockdown is 5636F2A1. This hash value is then encrypted into a cipher text. What A then sends is the message 'intelligent lockdown' and the cipher text. When the message reaches B, B first hashes the message 'intelligent lockdown'. This gives the hash value 5636F2A1. B then uses the corresponding key to unlock the cipher text. If B does this, the hash value of 5636F2A1 comes out. Exactly the same! Because B has two hash values that are the same, B knows that the message comes from A and that A wanted to send the message 'intelligent lockdown'.
If a hacker changes this message (or other data), the hash value will not match. Because if the data is changed slightly, the whole hash value changes. Suppose I adjust the message to 'intelligent lockdown!’ The hash value then becomes E2B7E1D4. This is completely different from 5636F2A1. Because the two hash values do not match, receiver B knows that the message has been tampered with.
Because the hashing technique is combined with the encryption technique, data can be sent in a secure way from person A to person B. This does not have to be a message, but can also be other documents, such as documents in the supply chain or tax returns and correspondence to the tax authorities.
I published this article previously on my LinkedIn page. This article was written on June 14 2020.
BTC address: bc1q3nnm8m2vrsv8med8a38dl37g8l3mm4wa7ph7wj
ETH address: 0x38b84E2D3B50F83A067A7488C1733180651f418A




Reactie plaatsen
Reacties